AWS Networking 101 — Securing your VPCs
In a previous post, we outlined the basic networking solutions offered by AWS to build isolated and secure private Networks on AWS. We also outlined how to provision Virtual Private Cloud (VPC) in AWS. In this post, we will outline how to utilize the different AWS security services in order [...]
Segment Routing 101 – Drivers and Overview
Introduction Can you list the different ways we can use to route traffic from point A to point B in the network? Some of the following methods may come to your mind first: hop-by-hop routing (with its flavours such as BGP hot-potato routing, and cold potato routing, and Strict routing [...]
Segment Routing – Building Blocks
Overview In the first blog of this series, we covered the Segment Routing Problem definition, Drivers, use cases, and the benefits it brings to the table. (for more details refer to this article). This post we will explain Segment Routing Building Blocks. without further ado let's start with SR SID. [...]
Segment Routing – Building Blocks Part 2
Overview In the first two articles of this series, we covered the Segment Routing Problem definition, Drivers, use cases, and the benefits it brings to the table. (First blog link Click Here). Then Segment Routing Building Block starts with SR SID (Second blog link Click Here) In this post, we [...]
Segment Routing Blog Series #4 – SR and LDP Interoperability
Overview In the first three articles of this series, we covered the Segment Routing Problem definition, Drivers, use cases, and the benefits it brings to the table. (First blog link Click Here). Then we explained Segment Routing Building Block starting with SR SID (Second blog link Click Here), and SR [...]
SD-WAN Security
Overview One of SD-WAN’s strongest capabilities is the remarkable ability to ability to secure unreliable Internet links and identify anomalous traffic flows and to bolster this strength, most vendors and SD-WAN technology providers are continuing to increase their native security features and to create robust ecosystems of network-security partners. However, [...]
5G Network Slicing – Moving towards RAN
Network Slicing is a 5G-enabled technology that allows the creation of an E2E Network instance across the Mobile Network Domains (Access, Transport, & Core). Each slice is ideally identified with specific network capabilities and characteristics. The technique of provisioning a Dedicated E2E Network Instance to End users, Enterprises, & MVNOs [...]
AWS Networking 101 — Automating AWS VPC Build with Ansible
In the previous post, we explained the main building blocks for AWS network infrastructure and how we can utilize AWS VPCs to build isolated and managed virtual Data Centers in the AWS cloud. In this post, we will outline how to design and build the AWS VPCs using Infrastructure as [...]
Segment Routing 101 – Drivers and Overview
Introduction Can you list the different ways we can use to route traffic from point A to point B in the network? Some of the following methods may come to your mind first: hop-by-hop routing (with its flavours such as BGP hot-potato routing, and cold potato routing, and Strict routing [...]
AWS Networking 101 – VPCs and Subnets
In this series of posts, we will explore the different networking solutions offered by AWS and how to build robust and highly available cloud solutions using the native Networking services offered by AWS. In this post, we will explore the basic building blocks of AWS infrastructure, and how AWS [...]
Tracking and Validating Configuration Deployment with NAPALM, Ansible and Git
In this post, we will outline a simple process for tracking configuration changes to network devices using Ansible. The goal is to provide a simple workflow for tracking, validating and approving network changes using Git as well as setting the stage for validation and testing. This can be considered part [...]
Network Devices Configuration Backup with Ansible and Git
In this post, we will outline how to use Ansible and Git in order to perform a simple workflow for device configuration backup for network nodes. Using Git as a distributed Version control and saving the device configuration into a Git Repo is one of the first steps into the [...]
CCDE / Network Design training. A student’s experience (part 2)
The second part of our feedback sharing from our students, today we present you with another email from our student’s thoughts as he shared his own training experience with us. "Hello and good morning/evening to you all. For me, the network architecture Bootcamp was more of a necessity than curiosity [...]
CCDE / Network Design training. A student’s experience.
With an effort to provide the best possible training experience, we asked our students to give us their feedback on their expertise both on technical and interpersonal aspects, and we were blown away by the great feedback we got, today we present you with one of our student’s kind words [...]
An interview with Mohamed Radwan (Part Two)
We continue our interview with Mr.Mohamed Radwan where was ask questions about soft skills, new technologies and network design, and the newest iteration of his famous CCDE exam. Enjoy the read! Mr. Radwan, the world of networking is drastically changing with the emergence of new technologies like IoT, SDN, NFV, [...]
An interview with Mohamed Radwan (Part One)
Today, we’ll be interviewing Mr. Mohamed Radwan, the award-winning network architect, and a top-notch consultant and trainer. Radwan is both a CCDE | CCIE certified individual with a curriculum too large to write in one go, Radwan is also one of the founders of Agile Integrated Solutions, an Australian-based IT [...]
9 Considerations to Size your routing domain (Number 9 will surprise you!!!)
It’s finally here, your dream job as a Network Designer in a newly established local service provider. You received the acceptance e-mail yesterday, and today is your first day on the job. After you take your time to explore your new workplace, you receive a call from your CTO asking [...]
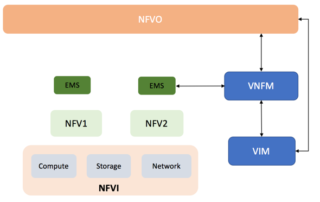
Why is it important to learn about NFV?
NFV is believed to be a main pillar of any enterprise digital transformation. Latest Market Surveys are all pointing to a wide adoption from Mobile Operators with ISPs. NFV Promise to fulfill the network need to provide a wide new services efficiently, dynamically, and with the least time to market. [...]
HOW TO AUTOMATE YOUR NETWORK USING ANSIBLE AND NAPALM – PART 3
In this article, we continue what we have started in the previous two articles focusing on Network Automation with Ansible and NAPALM. In the first article, we introduced Ansible and how it is used in combination with NAPALM to orchestrate a Multi-Vendor network. In the Second article, we illustrated the [...]
Using NFV to guard your “Environment”? — 4th / Last Episode
Test Results and Conclusion This is the last article in the series where we have discussed how to use NFV (Network Functions Virtualization) to secure your network and react promptly to security threats such as DDoS attacks. Before revealing the results of our PoC (proof of concept) lab, let’s [...]
How to automate your network using Ansible and NAPALM – Part 2
In the previous article, we introduced Ansible and how it can be used to manage network devices and how to use NAPALM as a common API to manage multiple vendor equipment. In this article, we will try to outline how to use Ansible and NAPALM to build a framework to [...]
How to automate your network using Ansible and NAPALM – Part 1
In the New Era of SDN and NFV and the push towards network programmability and automation, the usual method of deploying new changes on the network and validating the network state after this change will not scale. The way we interact with the network needs to be more dynamic and [...]
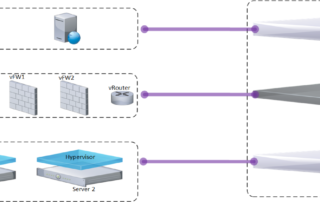
How to use NFV to Guard your “Environment”? — 3rd Episode
Test Methodology and Tools This Series of articles explain How to use emerging technologies such as NFV (Network Functions Virtualization) to secure your network and adapt promptly to security threats such as DDoS attacks. After we covered the problem statement, and requirements in the first article; we continued with the [...]
How to use NFV to Guard your “Environment”? — 2nd Episode
How to use NFV to Guard your “Environment”? -- 2nd Episode In this article, we will continue what we have started in the first article; How to use emerging technologies such as NFV (Network Functions Virtualization) to secure your network and adapt promptly to security threats such as DDoS attacks. [...]
FOUR TIPS TO PREPARE FOR THE CISSP EXAM
FOUR TIPS TO PREPARE FOR THE CISSP EXAM 1. Don’t jump to conclusions Read each question carefully. Think about it, analyse it, and finally, answer it. Even, if it seems to be a simple or easy question, I would advise you to read it at least three times, and give [...]
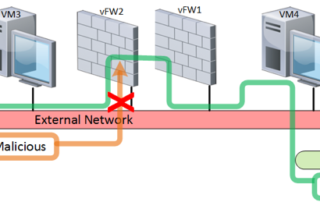
How to use NFV to Guard your “Environment”? — 1st Episode
How to use NFV to Guard your “Environment”? Believe it or not, we live in SDN/NFV era, as the famous clause says: “Software is EATING the world” seems to be funny, but it is actually happening ... Baed on that, How can we use SDN/NFV to secure the network [...]
CCDE Online Interative Training – Week2 IS-IS
CCDE Online Interactive Training launched on Saturday 22nd July with Solid Overview, Use Cases, and Design Considerations for the widely deployed OSPF. An Assignment and Discussion throughout the week around: - The maximum number of Routers in a single OSPF area, with justification. - The need for Segmentation, Layering, and [...]
New CCDE training will be coming soon, stay tuned.
CCDE Online Training CCDE is the pinnacle of design and networking architecture. Whether you are preparing for the CCDE exam or you are a Network Designer/Architect considering your options, this training is for you... All the details about the training will be revealed soon, stay tuned !!