How to use NFV to Guard your “Environment”? — 2nd Episode
In this article, we will continue what we have started in the first article; How to use emerging technologies such as NFV (Network Functions Virtualization) to secure your network and adapt promptly to security threats such as DDoS attacks.
The previous article starts with defining the problem statement, which can be briefed as: currently many networks are under serious threat of being confronted with an advanced DDoS attack using few hundred thousand of devices, Threat probability and expected impact increased exponentially due to the rapid increase in number of connected devices to the Internet (billions of devices, and the number is exploding since the wide deployment of IoT, and Drones)
Then we discussed the requirements of the study which is to examine the usage of NFV Technologies to mitigate the risk of DDoS attack. Tests have been conducted in our simulation lab.
P.S. we will describe the test-bed and test cases in the next article.
Architecture
Before revealing the architecture, let’s summarize the main goals of this test. The first and most important goal is to detect the DDoS attack as soon as possible to protect organization’s assets such as servers and network resources.
The second goal is elasticity, or in a simple language the ability to scale-up and scale-down network and servers’ resources according to utilization.
The third goal is mitigating and blocking this DDoS attack using NFV and security tools, which can be used as a first level of defence in case of DDoS attack.
Last but not least, the fourth goal is to block and stop illegitimate (DDoS) traffic, while minimizing the effect on legitimate (normal) users.
To achieve these goals we suggest the below architecture which align with ETSI / NFV Framework.
Let’s have a quick grasp on the existing DDoS solutions, available to companies and enterprises to secure their assets from DDoS.
Typical DDoS Solutions
Deploying a DDoS solution requires multiple components that needs to be integrated in order to deliver an end to end DDoS solution and there are multiple options to deploy such solution according to the tools you will use and the network that you are trying to protect.
For example, in Large service provider networks, a typical DDoS solution can be deployed using the following main components:
- Netflow or IPFIX that will be used to monitor the overall traffic flowing through the network and sending traffic samples to a centralized Netflow collector to analyze the traffic.
- Some of the existing solutions also utilize SNMP, and Routing Table (e.g. BGP routing table) to get better visibility of the Network and analyze the traffic traversing through.
- Dedicated DDoS mitigation solution like Arbor, that receives the NetFlow data and analyze this traffic and based on this traffic analysis it determines if a DDoS Attack is ongoing, based on this detection it can steer the subnet/prefix under attack to it (using prefix injection or BGP FlowSpec) in order to clean the traffic and return the legitimate traffic to its normal destination.
So, in a typical legacy DDoS solution, three main features must be present in order to deliver this solution
- A monitoring solution that monitor the health of critical services or customers.
- Detection mechanism in order to detect the DDoS attack.
- Mitigation/scrubbing node that stops the attack and send only clean traffic to the destination.
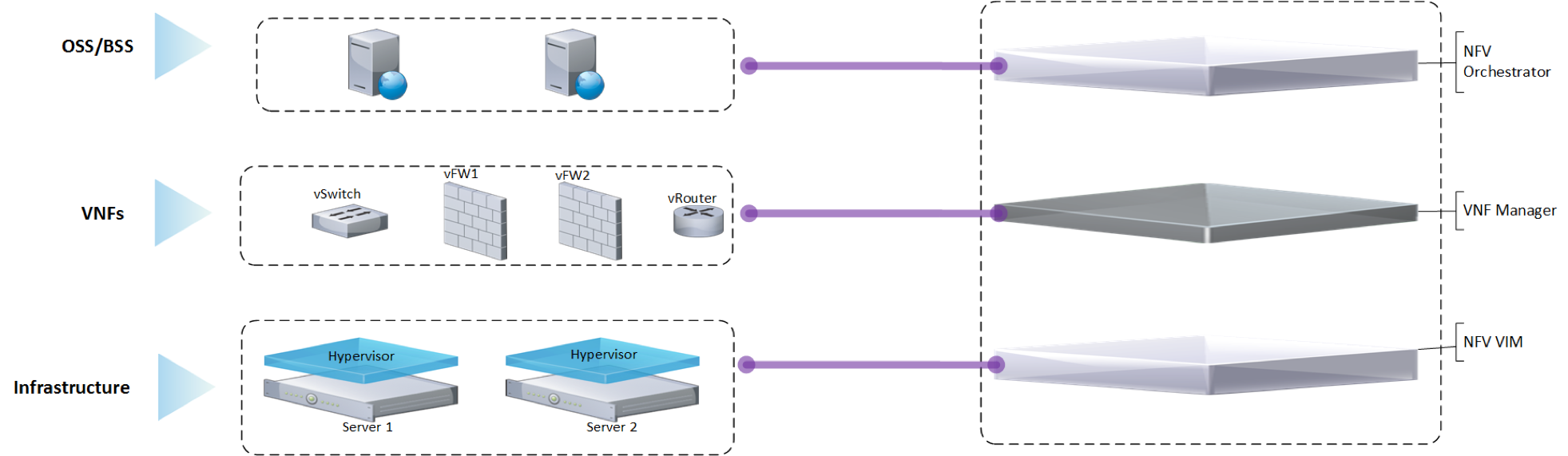
DDoS Solution using NFV:
Using the overall ecosystem developed by ETSI for NFV we can deliver the DDoS solution in a more elastic and dynamic approach where the overall solution can be adjusted according to the business needs and allowing much greater flexibility in the deployment.
ETSI MANO Architecture includes the following main elements:
- NFV Orchestrator
- VNF (Virtual Network Functions) Manager
- Virtual Infrastructure Manager
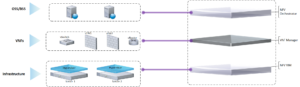
Note: for more information on ETSI NFV Architecture please refer to http://www.etsi.org/
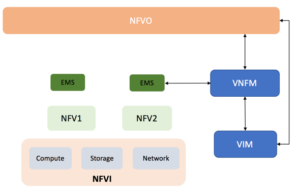
A closer look to the above Architecture in order to understand the building blocks and components of the NFV solutions includes the following:
In a typical NFV solution the main building blocks to deliver such a solution will be the following:
- VNF and in this case, it can be multiple VNFs like DPI for traffic detection and Firewall for Mitigation.
- VNFM which can be a Generic VNF to manage the Lifecycle of multiple VNFs or a multiple specific VNFM for each VNF and it provide the following main features
- Manage the Lifecycle of the VNF and perform Scale up and down for the VNF according to the configured KPIs.
- Provide the Day Zero configuration for the newly deployed VNFs.
- NFVO or the Orchestrator, which deliver the following main functions
- Monitor the end to end Service (DDoS in our case) and define the KPI of this Service.
- Define the service chain and how the different VNFs should be linked together to deliver the end to end service.
- Interface with the OSS/BSS layer to define which customer should be protected by this DDoS service and to monitor and trigger the enrolment of the customer for this service.
- VIM, which is the cloud OS over which the multiple VNFs will be on boarded.
- NFVI, which is the all the compute, storage and networking equipment which is managed by the VIM.
The below diagram outline how the different components interact with each other to deliver this end to end solution
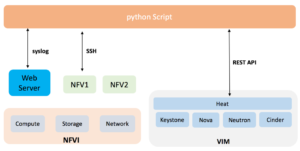
In our simulation lab, we started with a simple setup without the NFVO and VNFM and we used a python script to do a lot of the functions of both the NFVO and VNFM, we were concerned more which the ability the below key points:
- Ability to scale up and down the services (normally done by the VNFM)
- Ability to instantiate a VNF due to a pre-defined trigger (that can come from the NFVO)
- Ability to steer traffic to the new initiated VNF and dynamically insert and remove a VNF from the traffic forwarding path.
- Deploy day Zero configuration for the new initiated VNF.
In the setup, we used OpenStack as the cloud OS (VIM) to on-board the different VNFs that will be used as part of the DDoS Service. The below diagram outlines the setup used in our simulation lab to deliver the DDoS Server and how the python script interacts with OpenStack to deliver the required setup.
In the setup, the python script is performing the following function:
- Interact with the Heat REST API to drive the instantiation of new VNFs.
- Deploy the VNFs and deploy the day Zero configuration for those VNFs
- Monitor the CPU utilization of the Web Server (Customer/server to protect) to check if it is under attack or not.
- Interact with the Heat REST API to scale up and scale down the resources of the Web Server (Asset to protect) according to the CPU utilization and the threshold defined on the script.
- Control the VNF forwarding to steer DDoS traffic to be processed by the correct VNF to stop the attack.
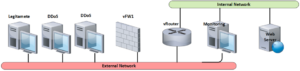
Simulation Lab Network Topology as shown in below diagram is composed of the following items:
Internal Network includes:
- Web server: simulate victim server
- Monitoring Station: monitor, control, and interface point with orchestrator.
- Virtual Switch: Layer2 connections.
- Virtual Router: Layer3 connection and routing traffic between external and internal networks.
External Network: includes 3 PCs:
- Legitimate user: simulate normal user trying to access webserver.
- DDoS users: simulate: malicious nodes, generating DDoS attack toward the webserver.
- Virtual Switch: Layer 2 connections
- virtual firewalls: Secure internal network
Design Considerations:
Finally, the main design considerations for our simulation lab are:
- The Webserver: a test page and test image will be used to check the service.
- Monitor machine has four tasks:
- Measure the traffic rate.
- Inspect the traffic.
- Integrate with NFV orchestrator to scale-up and scale-down the web-server CPU or Memory resources.
- Integrate with to the NFV orchestrator and VNF Manager to spin-off a new VNF.
- DDoS attacks simulated are:
-
- SYN flood
- HTTP-Get flood
This concludes this article; In the next one, we will discuss Test Strategy, and Test Cases along with the Tools used to conduct the tests.
To be continued …


Leave A Comment