In a previous post, we outlined the basic networking solutions offered by AWS to build isolated and secure private Networks on AWS. We also outlined how to provision Virtual Private Cloud (VPC) in AWS. In this post, we will outline how to utilize the different AWS security services in order to secure AWS resources.
Introduction
AWS employes a shared responsibility model for all the services and resources on AWS cloud, this shared responsibility means that parts of the overall security stack are managed by AWS and the other parts are managed by the customer. The level of responsibility shared between AWS and its customers depend on the type of service. The below diagram outline the shared responsibility model for Infrastructure Services like VPCs, EC2 Instances
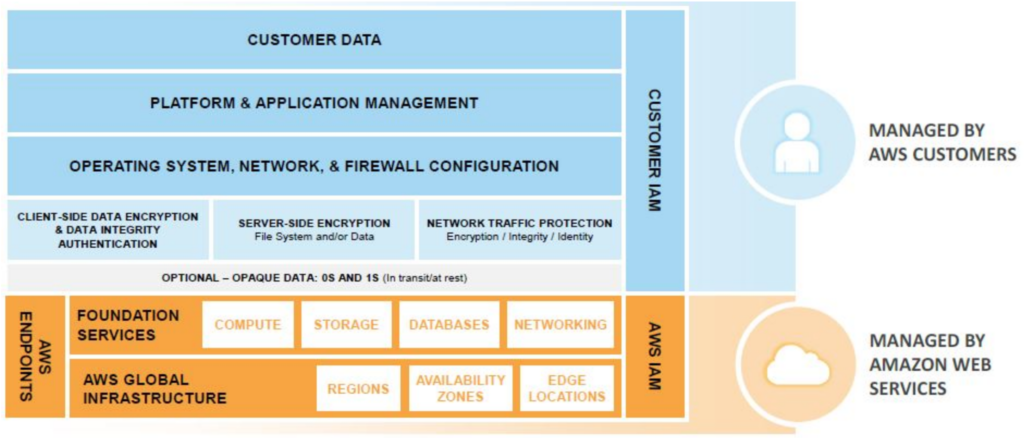
Infrastructure Security
Network ACL (NACL)
AWS NACL is very similar to the normal ACLs we configure on Routers to restrict traffic on a given interface, However, on the AWS they operate on the Subnet level within a given VPC. They can be used to increase the security posture of your cloud environment by selectively allow/deny specific sources/destination from communicating with the resources within a given Subnet. AWS NACLs have the following characteristics.
- They are bound to a given subnet and can be attached either on the inbound direction (traffic coming towards the Subnet) or outbound ( traffic from inside Subnet to outside).
- They are stateless, which means that for a given traffic flow to be allowed in and out of the subnet it must be permitted on both inbound and outbound NACLs.
- Only One NACL can be applied to a given subnet per traffic direction.
- NACLs can be configured to permit or deny traffic based on L3 and L4 IP header data.
- NACLs are VPC specific constructs, which means that a given NACL can’t be associated with different subnets from different VPCs.
By default in a given VPC, a default NACL is present which is attached to all the subnets within the VPC. AWS took the decision to simplify the network setup and thus configured this default NACL to allow traffic on both the inbound and outbound directions.
Security Groups (SG)
AWS Security groups is a host-based firewall which is attached to a given resource ( EC2 Instance, RDS Instance). The Security groups are attached to the ENI (Elastic Network Interface) which is attached to the instance and it filters the traffic on the inbound and outbound direction. The security groups have the following features
- They are attached to an instance and up to 5 security groups can be attached to a given instance. For a given traffic to be permitted it must permitted by all the SGs attached to the instance.
- SGs are statefull, which means if a given traffic is permitted on the inbound direction , it will be allowed on the outbound direction automatically and vise versa.
- SGs operation also on L3 and L4 IP information, however that can only be configured to permit traffic, they can’t be used to deny specific traffic flow (by default SGs deny all traffic).
- SGs are VPC specifc construct and they can operate within a given VPCs.
By default a default SG which denies all inbound traffic and allows all outbound traffic is configured within each VPC and it is attached to any new instance which is spawned in the VPC. Thus by default, any inbound communication to any instance within AWS is filtered by this default SG. This default SG must be adjusted in order to allow at minimum SSH traffic so as to be able to manage the instance.
The below diagram outline the interaction between Security groups and NACLs within the AWS VPC.
Identity and Access Control
Identity and Access Management (IAM)
Monitoring and Logging
VPC Flow logs
VPC Flow logs are very similar to NetFlow in traditional networking. They provide deep insights on the traffic flow within the VPC and all these flow logs are collected and stored within a given S3 bucket that you specify for further analysis or sent to CloudWatch Logs.
VPC Flow logs can be configured to capture traffic on a VPC, Subnet or Instance interface level. In case it is configured on a VPC level, all network interfaces for all the instances in the VPCs will be monitored. It records the 5-tuple information that identifies a given traffic flow (srcIP, dstIP, srcPort, dstPort, and Protocol) as well as it provides the packet count and a number of bytes for this traffic flow.
Any traffic allowed by the Security group and NACL is recorded by the VPC Flow logs as Accept and any traffic reject by a Security group or NACL is also recorded as Reject.
AWS CloudTrail
AWS CloudTrail can be compared to Radius Accounting in traditional networking, where we want to understand and log all the user activity within the AWS environment. Any interaction with any resource within AWS is through an API call to the AWS orchestration system. All these API Calles are logged by cloudtrail in order to provide insights regarding user activity and to provide compliance and audit checks on all the resources within the AWS account.
Any modification to any resource within the AWS account like creating a VPC, creating a security group or any other action is logged by default by cloudtrail as an event.
AWS CloudWatch
Conclusion
Sources
AWS VPC Flow Logs
https://docs.aws.amazon.com/vpc/latest/userguide/flow-logs.html#flow-log-records



Leave A Comment